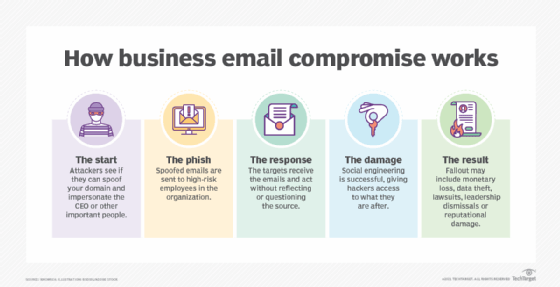
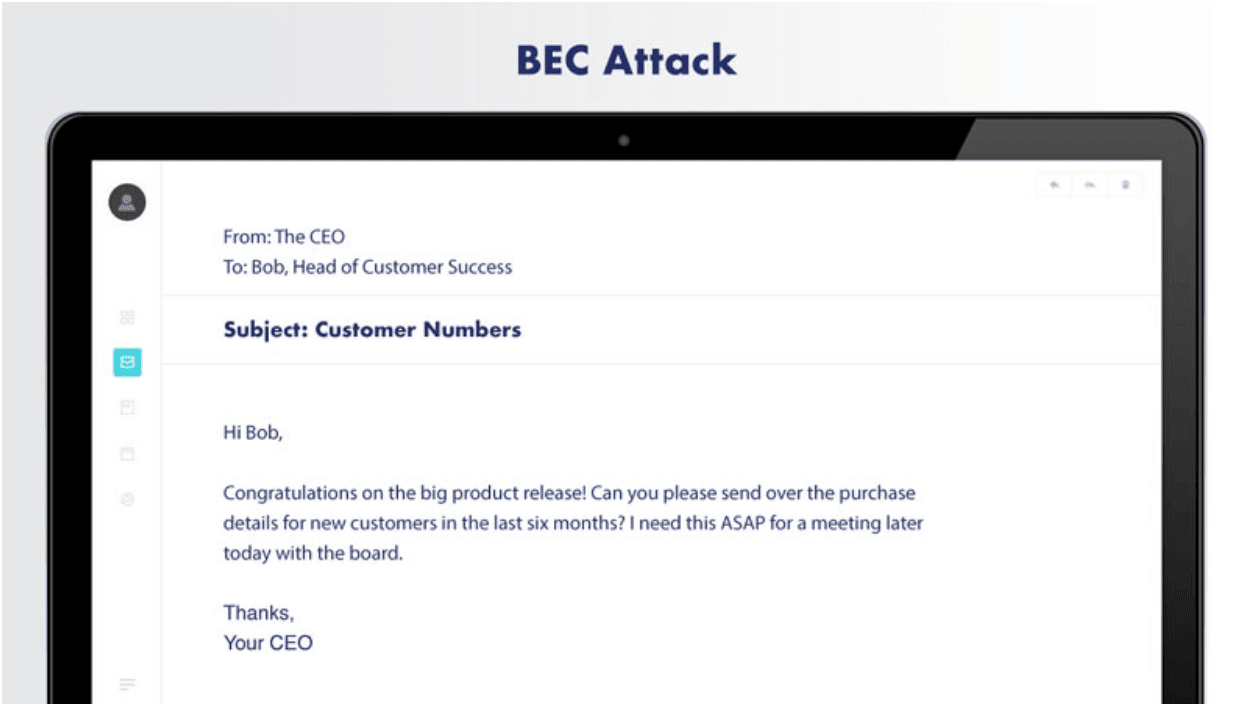
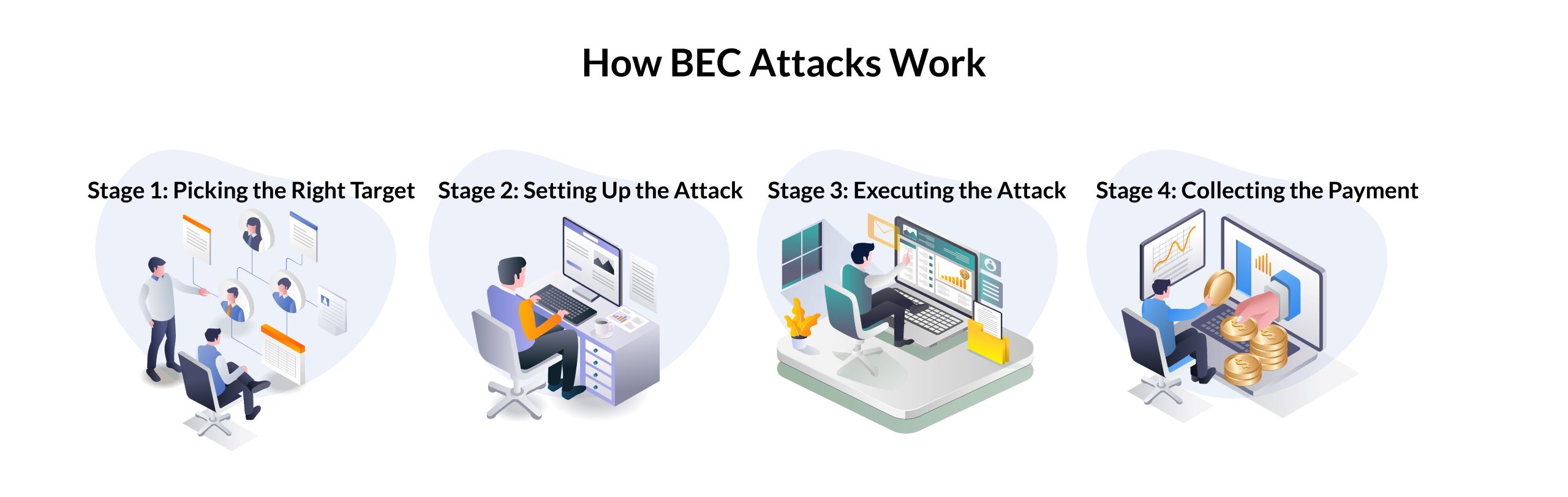
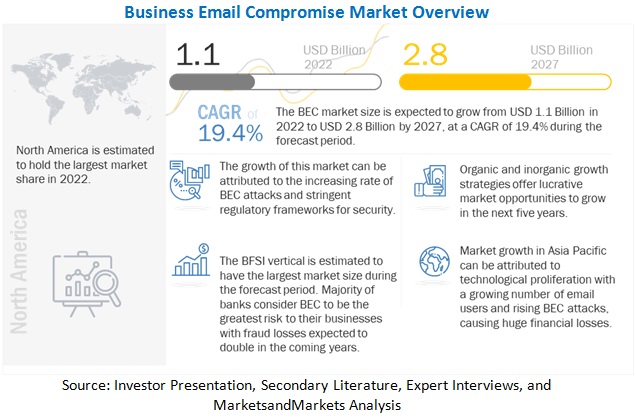
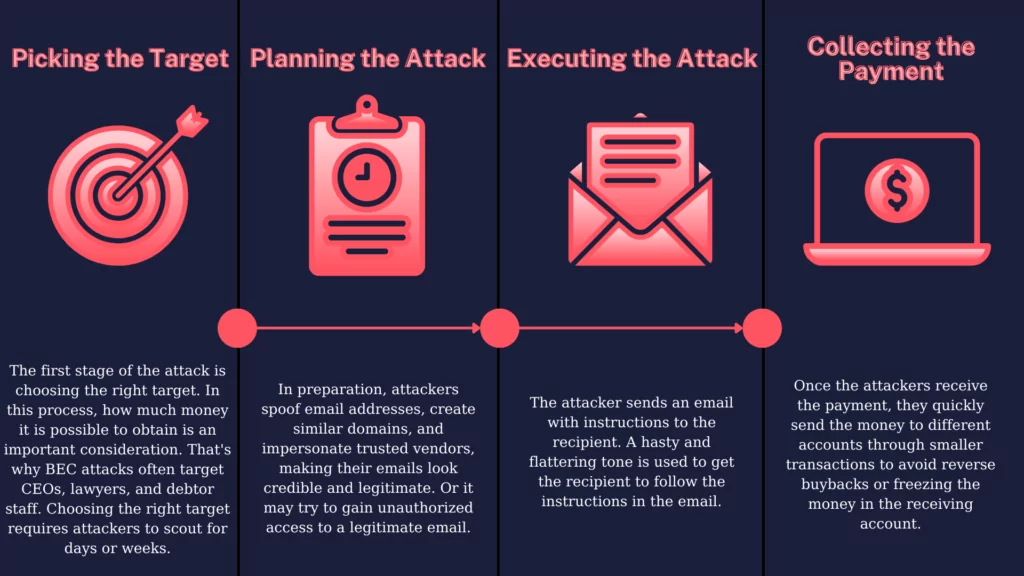
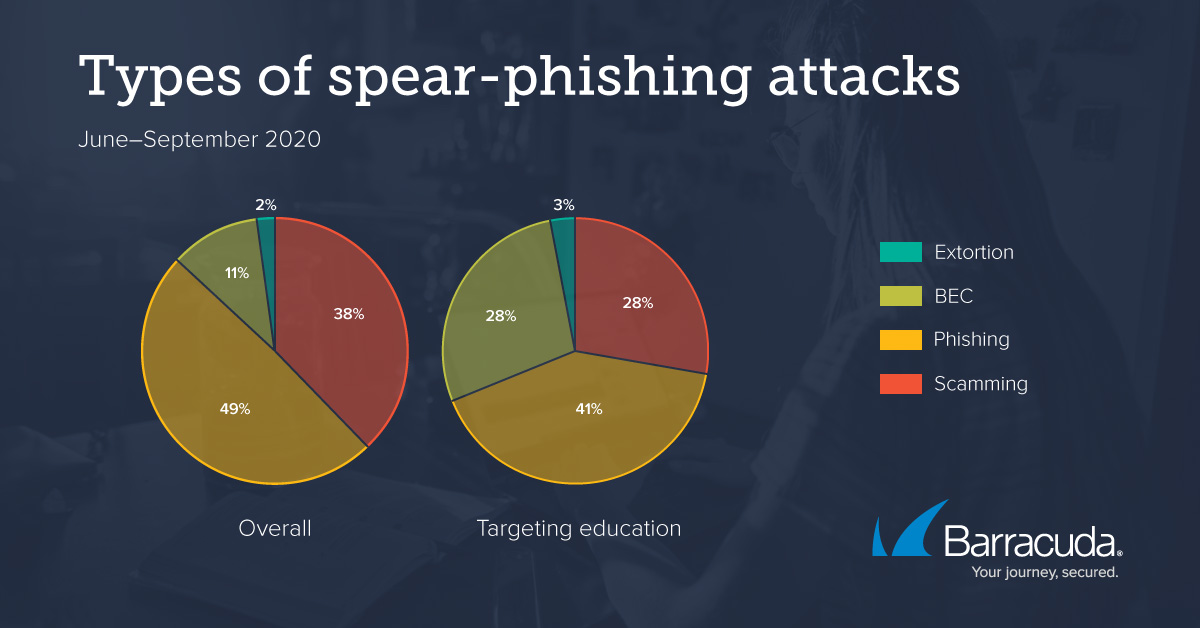
Armorblox Email Security Threat Report Reveals 72% Rise in Business Email Compromise Attacks in 2022
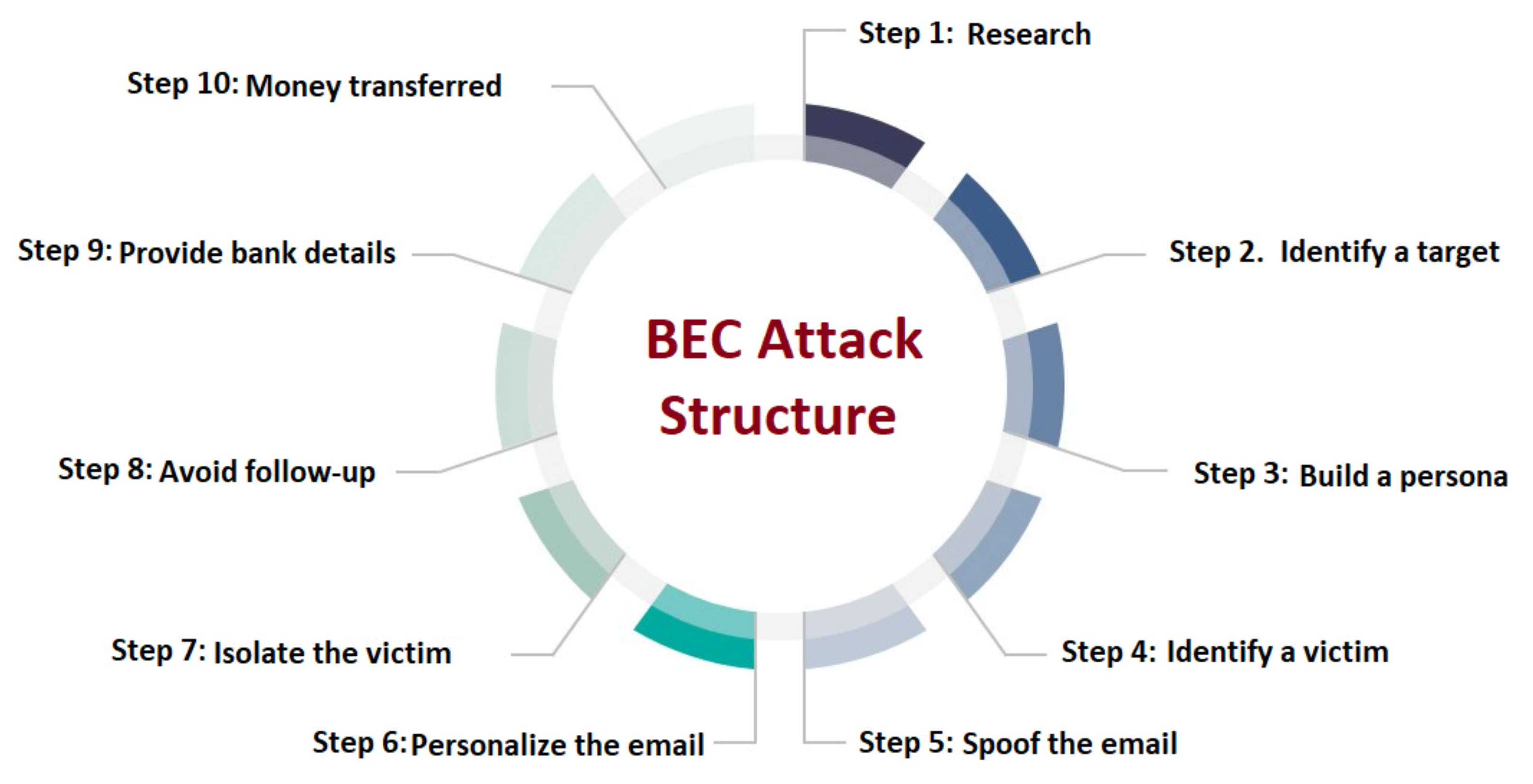
Electronics | Free Full-Text | Business Email Compromise Phishing Detection Based on Machine Learning: A Systematic Literature Review

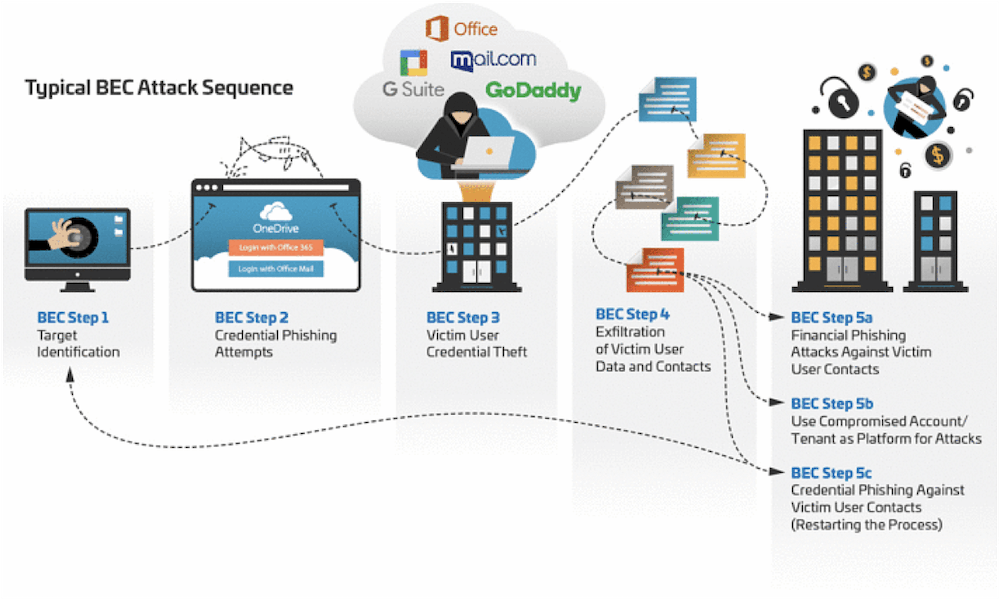
Business Process Compromise, Business Email Compromise, and Targeted Attacks: What's the Difference? - Security News




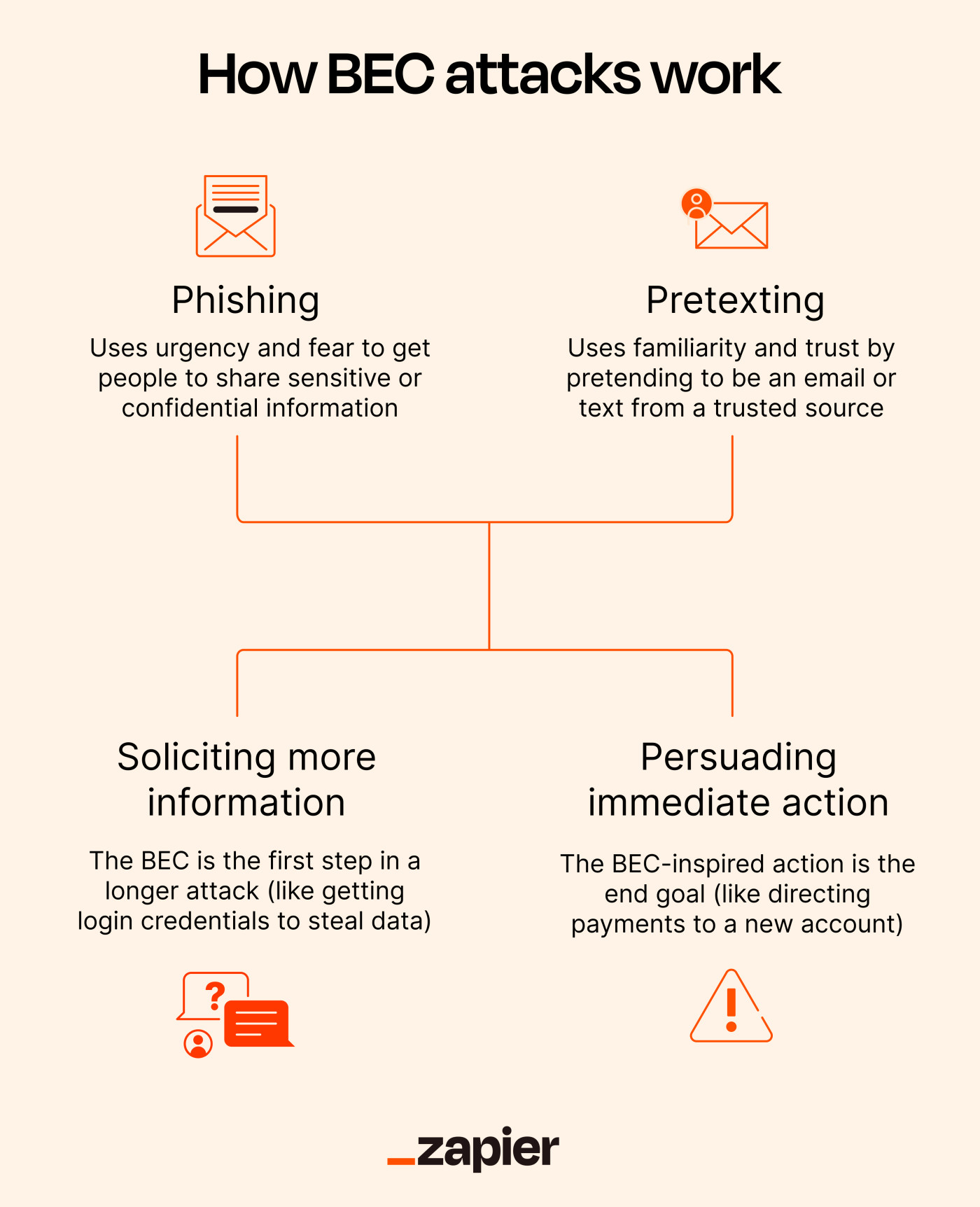




.png)